
With another year of fast technological evolution ahead of us, cybersecurity continues to be at the forefront of news headlines. As the supply chain grows more complex and regulations evolve at a rapid pace, it is crucial for organisations to adopt the right approach towards cybersecurity. It all begins with awareness as a majority of security breaches stem from a human element. With social engineering on the rise, fuelled by the explosion of artificial intelligence, organisations must be better equipped to tackle such threats. While technology can only provide so much defence, organisations must build stronger and more robust layers of defence that include both technological and human elements. Timely patching of devices to reduce exposure to vulnerabilities is an essential part of best practices, but a culture that fosters greater cyber awareness is equally critical. Companies must embrace such a culture to be better prepared for any cybersecurity challenges that come their way.
One of the most pressing concerns is how cyber criminals will utilise AI in the coming years. Platforms such as ChatGPT and its competitors have gained immense popularity due to their ease of use and constantly improving writing capabilities. However, the downside to this technological advancement is that it will enable phishing groups to create more sophisticated cyber-attacks and phishing emails. Historically, these attackers have struggled with language barriers, but AI can now help them generate content in languages beyond their own, and with increased accuracy. Additionally, the vast amount of open-source intelligence available online makes it easier for criminals to launch targeted phishing attacks against specific individuals. The danger doesn’t stop there – generative AI can even create code that can serve as the basis for malware. Although platforms like ChatGPT claim to refrain from creating criminal code, chatbots can be tricked into creating nefarious code by malicious users who tailor their prompts. Even more concerning is the possibility of criminals building their own language models based on existing malware code from the dark web, which would significantly increase their ability to deploy software as part of attacks.
As we move towards 2024, it is crucial for enterprises to focus on cybersecurity. To ensure a safe and secure environment, AWTG listed a few things that organisations need to consider.
Firstly, in today’s interconnected world, where digital threats are constantly evolving, one concept has gained paramount importance – the Zero Trust Architecture (ZTA). AWTG recognises the significance of ZTA as it aligns with our commitment to addressing cybersecurity concerns comprehensively. Zero Trust Architecture is a security framework that operates on the principle of “never trust, always verify.” This means that in the world of cybersecurity, trust is no longer assumed, even within an organisation’s network. Instead, every user, device, and application are treated as potentially untrustworthy until they prove otherwise. This paradigm shift is critical, as even trusted users can gain unauthorised access to sensitive data. The traditional perimeter-based security measures like IPSec, firewalls, VPNs, and IDSs, which focus on protecting the network’s edges, fall short in ensuring comprehensive network security. With the advent of 6G, expected to be a more open network compared to previous generations like 5G and 4G, the distinction between the inside and outside of the network becomes increasingly blurred, underlining the urgency of adopting ZTA principles.
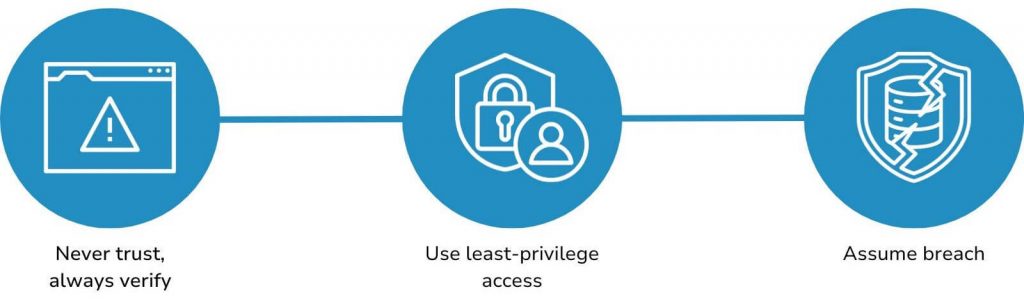
Zero Trust Architecture mitigates this risk by continuously monitoring user behavior and limiting access based on need and behavior, even for trusted employees. Zero Trust Architecture principles include granting users the minimum necessary access, granular network segmentation to prevent lateral movement, continuous user and device authentication, strict access controls, data encryption, and addressing insider threats alongside external threats.
At AWTG, we are dedicated to highlighting and addressing cybersecurity concerns. We have adopted a security architecture based on the Zero Trust model, which means that we treat every aspect of our network and operations with the highest level of skepticism. This approach allows us to provide our clients with cutting-edge security solutions that safeguard their digital assets in an ever-evolving threat landscape.
Building upon our commitment to cybersecurity, there is a second critical imperative for enterprises as we approach 2024 – Strategic Data Management. In this era of constant digital evolution and escalating cyber threats, organisations must invest in reliable data management systems to organise, safeguard, and harness the power of their data. A scalable data management strategy is not just advantageous but indispensable to meet the insatiable demands for instant access and AI-driven insights. AWTG, in alignment with its dedication to cybersecurity, plays a pivotal role in providing the privacy and security needed for data in this ever-evolving landscape. Our expertise encompasses implementing data encryption, strict access control, data classification, and Security Information and Event Management (SIEM) solutions as essential components of a comprehensive security-focused data management strategy.
Finally, information is essential in maintaining a robust security strategy. In AWTG, we conduct regular and brief security awareness training sessions and notifications that help employees recognise and avoid potential threats. Educating employees on all departments on safe password behaviours and other critical security topics is extremely important.
In conclusion, enterprises must remain vigilant and proactive when it comes to cybersecurity. By taking small but significant steps, investing in Zero Trust Architecture, robust data management systems, and prioritising information, organisations can ensure safety in the constantly evolving digital landscape of 2024 and beyond.
